“Database migration between Standalone and Management only machines is not supported”
The error above is observed when trying to migrate the management from a standalone firewall to a new Smartcenter for distributed architecture and appears to be more of a bug than anything else.
Luckily it is easily sorted:
1. Take an export of existing standalone management & firewall:
Download newest migration tools from https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk91140 and run an export:
# $FWDIR/bin/upgrade_tools/migrate export MY_EXPORT
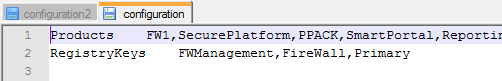
2. Extract the files from the MYEXPORT.tgz using e.g. 7zip. Using Notepad++ or similar, change the “configuration” and “configuration2” files to take the Firewall element out as shown in the pictures below:
Remove the “Firewall” string in “configuration” ..
.. to look like this:

And change the following strings in the “configuration2” file ..
3. Repackage the files into MY_NEW_EXPORT.tgz, copy them on to the new management center and run the import:
# $FWDIR/bin/upgrade_tools/migrate import MY_NEW_EXPORT
Job done!